So, somebody ((Very different from myself, naturally)) forgot the administrator password to an OpenAM installation, and I needed to reset it. This is not a supported operation, and in the interest of being positive, let’s just say it was a journey with opportunities to make it work…
First, this procedure works with a single OpenAM server using externalized storage. If either of these is not true for you, there is no guaranteeing whether it will work. I’ve done this on OpenAM 10 and 12; according to this blog

The
Instead, we need to generate a new password using this brilliant tool. It requires we pick up the configuration encryption password and manually replace it.
Now, even using externalized user storage, OpenAM comes with its own LDAP storage, where this is stored. To access this, you need access to this storage using a password that we also don’t have access to. The good news is, we can get access to this storage.
We can generate a new password using the command
<openam>/opends/bin/encode-password -s SSHA512 -c '<new password>'
This will spit out a (salted) hash looking a bit like this:
Encoded Password: "{SSHA512}ZgkejixlHe6I7W33Zj0sYd5rmFiE8hVC2Vym0Z/O6XC3kZF3F8DT+GvezudhSMNLwHcIDDvq2+F2m4J6elAFF6CkyC/VQ9+J"
Keep track of this. Then open <openam>/opends/config/config.
dn: cn=Directory Manager Copy,cn=Root DNs,cn=config
objectClass: person
objectClass: organizationalPerson
objectClass: inetOrgPerson
objectClass: top
objectClass: ds-cfg-root-dn-user
userpassword: {SSHA512}ZgkejixlHe6I7W33Zj0sYd5rmFiE8hVC2Vym0Z/O6XC3kZF3F8DT+GvezudhSMNLwHcIDDvq2+F2m4J6elAFF6CkyC/VQ9+J
givenName: Directory
cn: Directory Manager Copy
ds-cfg-alternate-bind-dn: cn=Directory Manager Copy
sn: Manager
ds-pwp-password-policy-dn: cn=Root Password Policy,cn=Password Policies,cn=config
ds-rlim-time-limit: 0
ds-rlim-lookthrough-limit: 0
ds-rlim-idle-time-limit: 0
ds-rlim-size-limit: 0
After this little joy, restart OpenAM. Now, you can open your LDAP browser (I’m evaluating this one) to port 50389 (on my installation) using the user you created and the spiffy new password.
Navigate to the key suggested by the tool page, and copy the encryption password (blanked out but from the red rectangle):
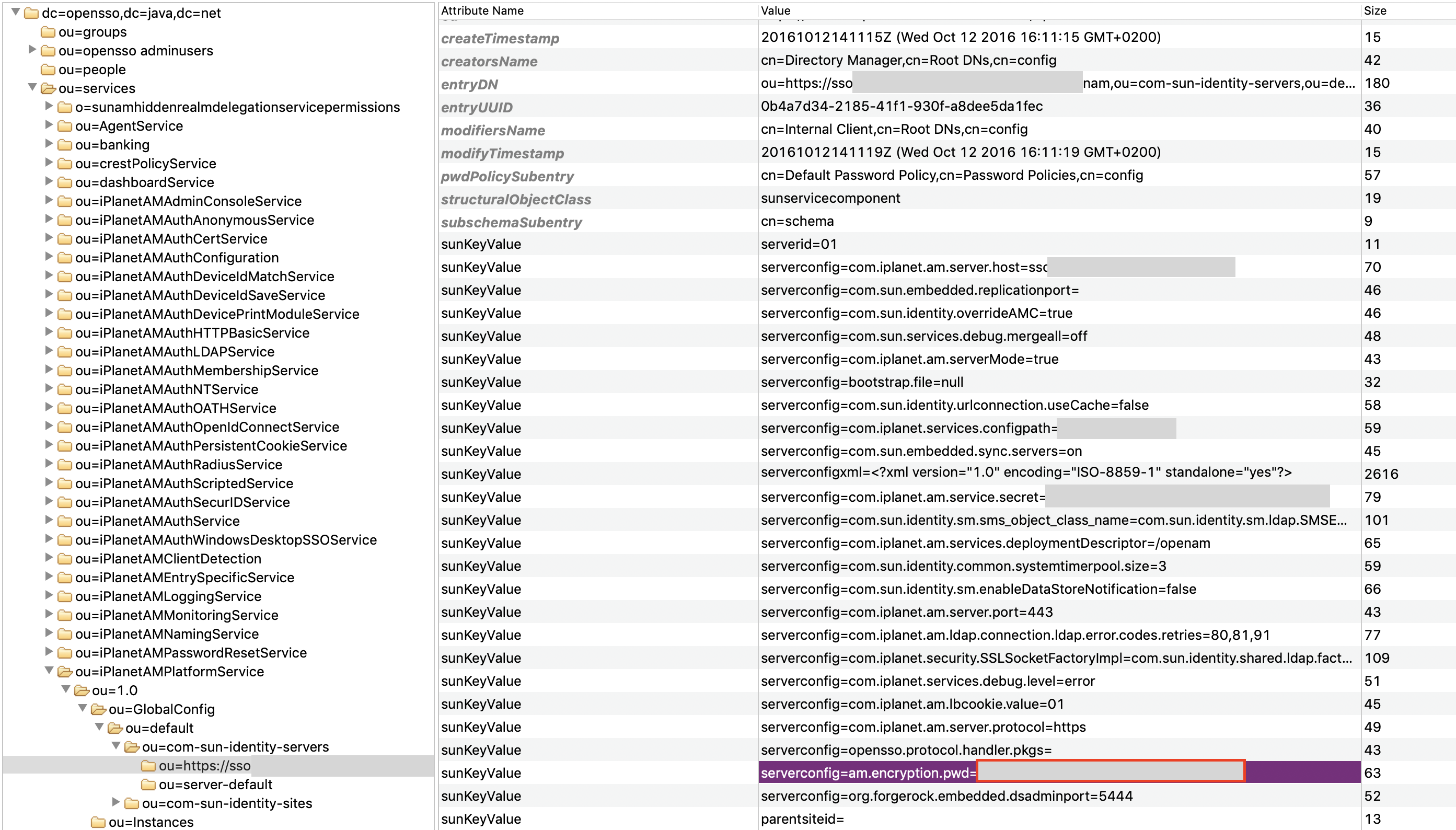
Notice you do not want the also good-sounding password from the “serverconfig=com.iplanet.am.service.secret” but the one from
javac AmAdminPwdGen.java
java AmAdminPwdGen -k '<code from LDAP>' -p '<new amAdmin password>'
Finally, put that in on the password key also indicated on the tool page:
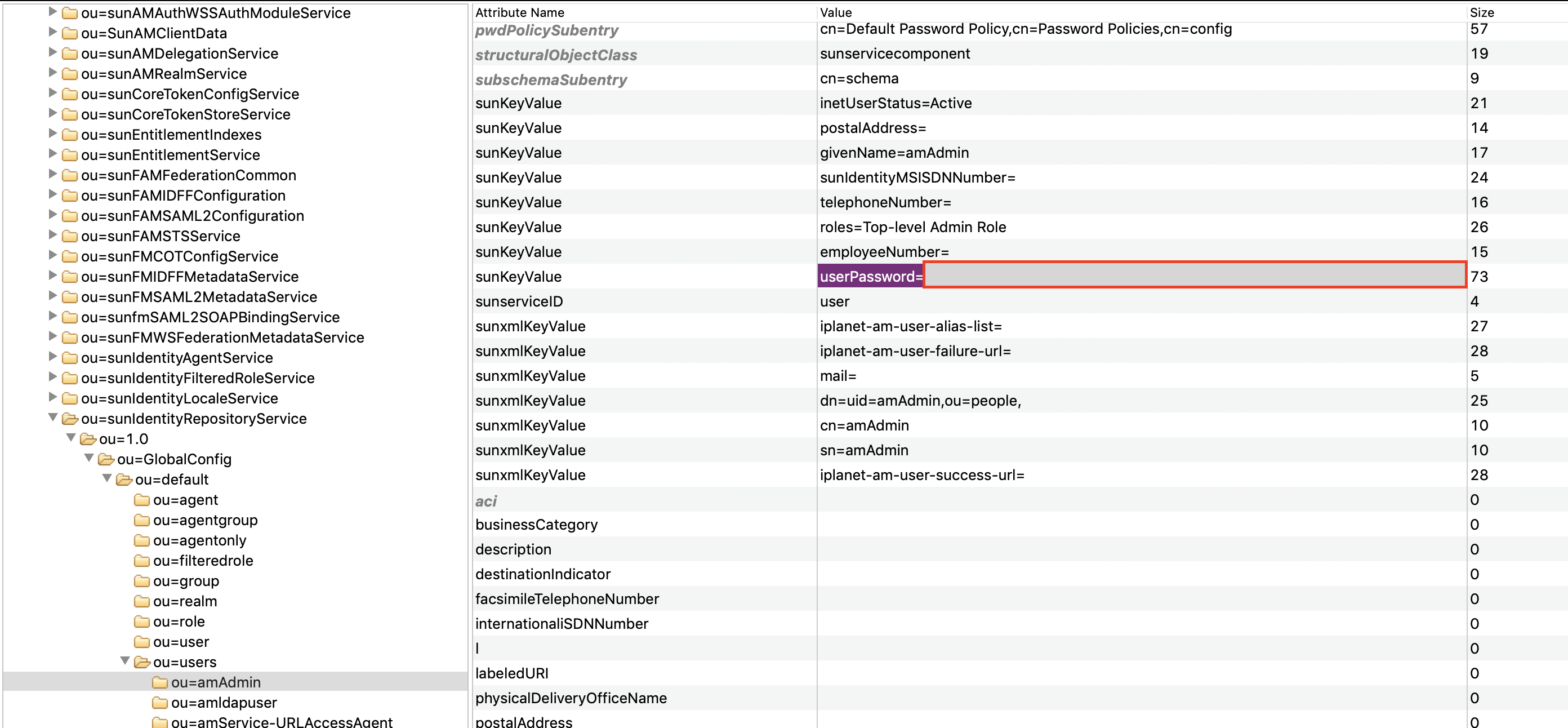
You have to retain the “userPassword=” part of the key even though the password generation tool doesn’t. Finally, restart OpenAM and you can now log in with your fancy new password. Hopefully.

